Software CEO charged with stealing massive amounts of election data in Los Angeles, sending it to China
10/20/2022 / By JD Heyes

The CEO of a small Michigan-based firm has been arrested and charged with allegedly storing a large amount of data on Los Angeles County poll workers on servers that are based in China, in what prosecutors have said is likely the biggest data breach in American history.
After Eugene Yu, who heads up election software company Konnech, was charged, Los Angeles County prosecutor Eric Neff alleged that the amount of data involved in the breach was “astounding,” adding that “this is probably the largest data breach in United States history.”
“Based on evidence recovered from a search warrant executed October 4, 2022, the District Attorney’s Office discovered that Konnech employees known and unknown sent personal identifying information of Los Angeles County election workers to third-party software developers who assisted with creating and fixing Konnech’s internal ‘PollChief’ software,” says the complaint, according to KaneKoa The Great’s Substack.
The complaint goes on to state that Luis Nabergoi, a Konnech project manager who oversaw the Los Angeles contract, wrote in a Chinese-owned messaging app that “any employee for Chinese contractors working on PollChief software had ‘superadministration’ privileges for all PollChief clients.”
Retired career CIA officer Sam Faddis explained on his substack what it means to have super administrator status:
An individual with super administration access to a system can do effectively anything inside that system. He or she can delete data, steal data, alter data, change programming, etc.
Perhaps most importantly, that individual can cover his or her tracks, because they can potentially also access and alter all security protocols and programs.
So, Konnech, which has numerous questionable ties to Chinese entities was allowed to punch a hole into our election systems, and then Konnech was allowed to grant that same level of access to unknown “contractors” in China.”
In Los Angeles alone, there were “probably thousands of victims,” Neff said. “They have contracts all over the country.” He added: It’s “a massive data breach.”
The connection was initially discovered by Catherine Engelbrecht of TrueTheVote and Gregg Phillips of OPSEC, both of whom were heavily involved in Dinesh D’Souza’s blockbuster 2020 election fraud documentary “2,000 Mules.” They recently shared the story of how they were involved in what they described as a 15-month counterintelligence operation with the FBI to uncover evidence that Konnech was working with China. After the FBI turned against them — probably because they worked with D’Souza on his documentary — the pair sought out others with whom they could share their knowledge of the investigation’s findings.
Neff argued against bail for Yu, a naturalized American who was born in China, for fear that he may be able to return to his home country, where he lived for 33 years and had business operations. Neff added that Yu’s alleged crimes pose “a broad danger to the community.”
“He has extensive friends and family contacts out there,” the prosecutor said, according to The Epoch Times. “The company is still operating, still uses Chinese contractors to conduct its business.”
The outlet notes further:
Konnech first began supplying poll worker management software to Los Angeles County in 2019. In October 2020, Yu’s company entered into a $2.9 million, five-year contract with the county. The contract required Konnech to keep the county’s data in the United States and allow access only to U.S.-based staff who are citizens or lawful permanent residents, according to the Los Angeles County district attorney’s office.
Despite these obligations, Konnech employees were sending personal identifying information of Los Angeles election workers to third-party software developers in China “who assisted in creating and fixing” Konnech’s software, known as PollChief, according to the complaint filed by California prosecutors on Oct. 14.
In August 2021, the L.A. County election office posted a network diagram of its Election Management System (EMS) that is called “EMS Future State v15” to the county registrar office’s web site. The diagram is essentially a digital roadmap that shows how data flows within an organization. “If Los Angeles county’s uploaded diagram is accurate, it demonstrates that Konnech’s PollChief software has a direct ‘data integration’ and ‘data exchange’ point with the county’s overall EMS software,” notes KaneKoa The Great, who added:
According to the county’s diagram, PollChief appears to integrate with; “Voter Registration,” “Voter Records,” “Election Night Reporting,” “Address Verification,” and “Ballot Layout,” among other data that moves to that same “data integration” and “data exchange” point.
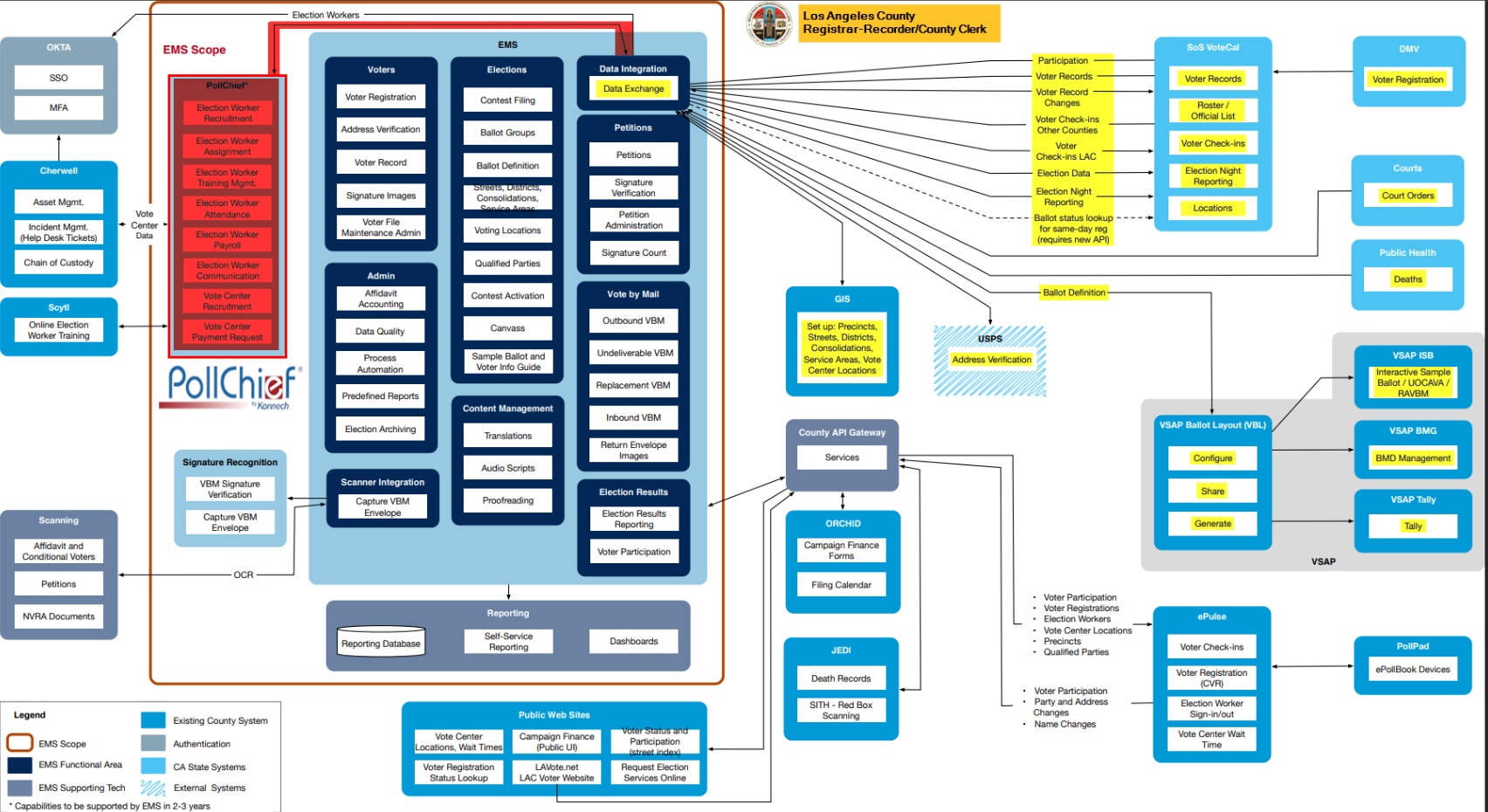
A team of software developers, engineers, and data scientists at electionfraud20.org who study election system vulnerabilities has stated that Los Angeles county’s diagram indicates that “you are giving massive back-door access to all the critical election subsystems that are required to rig the election, in a way that no one will ever notice. And you are giving it to Chinese developers.”
“If PollChief is compromised, this diagram shows that the whole election management system is compromised,” the data team noted further.
The bottom line is this: Any company with any ties whatsoever to China should never get within 100 miles of a U.S. election data system.
Sources include:
Submit a correction >>
Tagged Under:
2020 election, China, conspiracy, corruption, deception, election data, election software, FBI, Konnech, Los Angeles County, national security, rigged, stolen data, vote fraud
This article may contain statements that reflect the opinion of the author
RECENT NEWS & ARTICLES
COPYRIGHT © 2017 SPYGATENEWS.COM
All content posted on this site is protected under Free Speech. SpygateNews.com is not responsible for content written by contributing authors. The information on this site is provided for educational and entertainment purposes only. It is not intended as a substitute for professional advice of any kind. SpygateNews.com assumes no responsibility for the use or misuse of this material. All trademarks, registered trademarks and service marks mentioned on this site are the property of their respective owners.




















